Cain and Abel Software For Password Recovery
Cain and Abel software is powerful password recovery software of any operating software.it is used for cracking password by sniffing of networks.
1/31/20255 min read

Cain and Abel Software
According to the original and official website, Cain and Abel Software is a password recovery software for operating systems.
Sniffing the networks allows for recovering different types of passwords using dictionaries, brute-force, and cryptanalysis attacks. It can record VoIP conversation and scramble passwords.
It decodes wireless network key recovery, and with the help of routing protocols, it uncovers the cache passwords. The most current version is quicker and has various updated features, such as Man-in-the-Middle attacks and ARP (ARP Poison Routing).
It helps in sniffing over changed LANs. This version of the sniffer has filters to obtain data from multiple authentication methods and ways and can also scan encrypted protocols like SSH-1 and HTTPS passwords.
It includes hash calculators, cryptanalysis, password decoders, routing protocols authentication monitors, route extractors, dictionaries, and brute-force crackers for all famous hashing algorithms and a minimum set of standard network and system security tools. These are also included in the latest version.
Who needs to utilize this tool?
Network administrators, educators, professional penetration testers, security consultants, forensic personnel, and security providers will find Cain and Abel a helpful tool.
Requirements for Cain and Abel
To properly set up Cain and Abel, the following requirements of the system are necessary to meet the desired results:
10 MB or larger space* on the hard drive.
Windows 2000, XP, 2003, and Vista OS.
Packet driver for WinPcap (v2.3 or higher).
AirPcap Packet Driver* (for WEP crackers and passive wireless sniffers) setup.
How to Install?
Download Cain and Abel
Go to the Cain & Abel page
Visit: [www.oxid.it/cain.html](http://www.oxid.it/cain.html)
After downloading, run the self-installing executable package and proceed with the given instructions to execute.
Some Important Features of Cain
All of Cain's capabilities that make it an excellent tool for network penetration testing are listed below:
Manager for secured storage password decoder for credential manager passwords.
LSA trade secrets decoder for dumper dial-up passwords.
Service manager poison routing (ARP).
Network enumerator with route table manager.
SID scanners monitor of remote registry sniffer routing protocols.
Advanced Features
APR Full RDP Session Sniffer
APR Full SSH-1 Session Sniffer
Password decoder for Cisco Type 7 and Rainbows Crack internet client.
Password decoder for Cisco VPN clients.
Hash calculator for RSA security tokens.
View for TCP/UDP Tables (ICMP, UDP, and TCP traceroute).
SNMP/HTTP Cisco configuration downloader/uploader.
Revealed a wireless zero configuration password decoder for a dumper remote desktop.
Hashes MAC for MSCACHE, the dumper password extractor for MySQL.
Oracle password extractor, Microsoft SQL Server, and VNC password decoder.
Syskey decoder.
What is MAC, sniffing, ARP?
MAC:
Media Access Control. ARP, a famous protocol, translates IP (Internet Protocol) addresses to MAC.
ARP:
Address Resolution Protocol (ARP) enables networks to deliver data specific to any device. It helps connect a device with a router or gateway.
Sniffing:
This is a cybersecurity type that allows hackers to steal data over a network by using sniffer packets.
Uses:
After launching, we must set up the application to use the proper network card. Knowing the MAC address of the network card you plan to utilize for the sniffer is preferable if you have many network cards. Follow these steps to obtain your network interface cards MAC address:
Type "ipconfig /all" as the command.
To help choose which NIC to use in the Cain program, get the MAC address of the necessary Ethernet adapters, write it down in Notepad, and then utilize this information.
On the main menu, select Configure now. When the configuration dialog box opens, you can choose the preferred network interface card.
Reviewing The Setup Dialog's Tabs
Certificate collector tab:
This tab gathers all certificates sent and received between servers and clients by configuring proxy IPs and listening ports.
Challenge spoofing tab:
You can construct a unique challenge value on this page, which will be rewritten into NTLM authentication packets. Cain's toolbar makes it simple to activate this feature, which needs APR. A predefined challenge can be used to crack NTLM hashes that are gathered on the network using Rainbow Tables.
Cracking passwords:
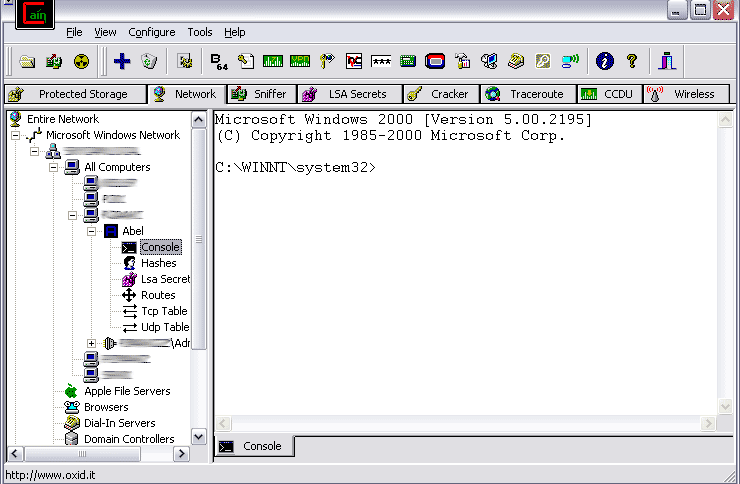
It's time to discuss Cain's most crucial feature, the cracker tab. Cain automatically transmits passwords for all supported protocols, including LM and NTLM hashes, to the Cracker tab as it captures them. We shall import a local SAM file for demonstration purposes only to demonstrate this point. To import the SAM file, follow these steps:
The four NTLM and LM hashes that will look like the following image are as follows:
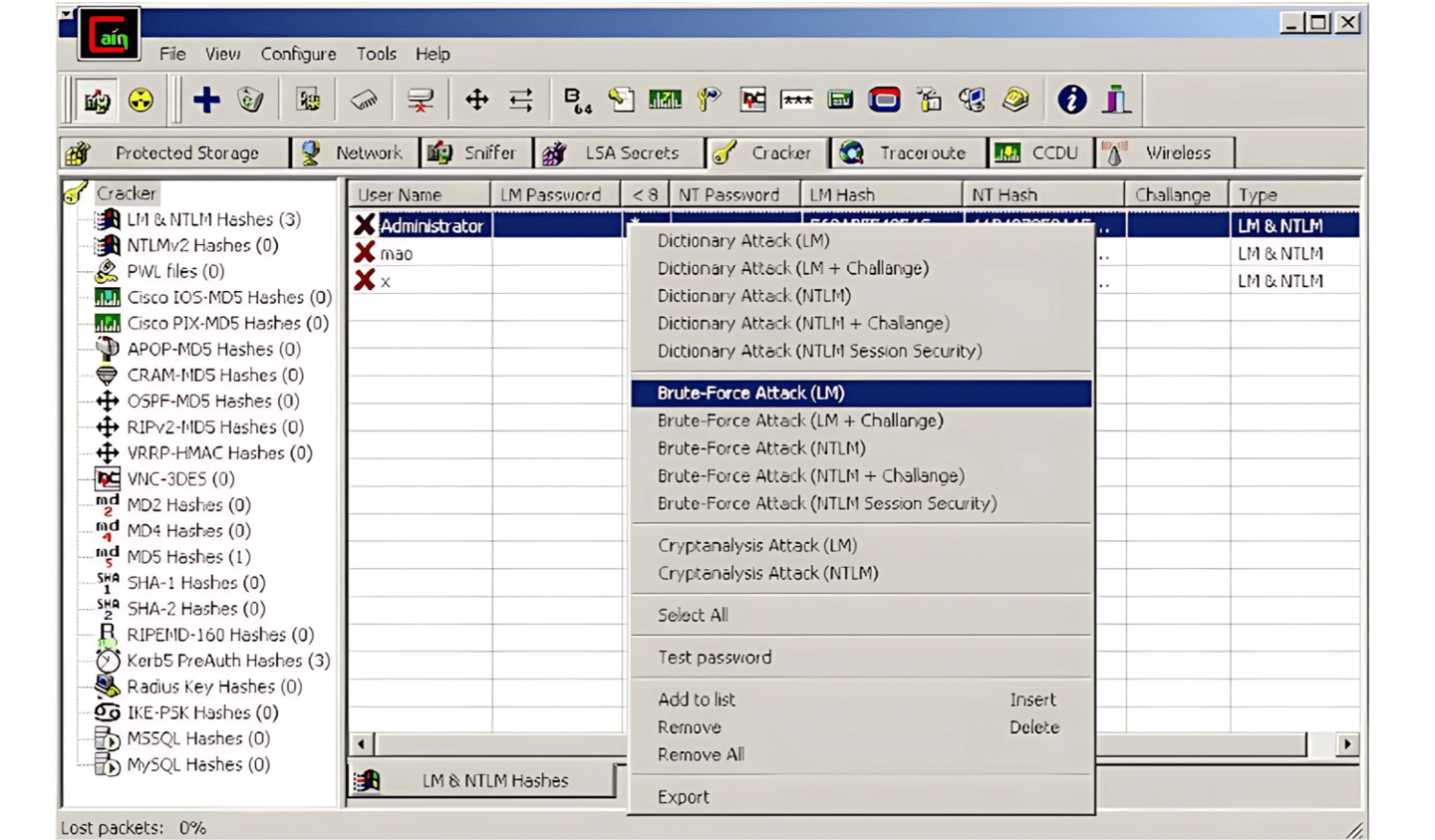
Additionally, the following picture contains every password strategy that might be used:
The figure above illustrates the various highly successful methods of cracking passwords. We will examine each method's definition.
Dictionary attack:
A dictionary attack employs a focused method of repeatedly attempting every word in a comprehensive list known as a dictionary (from a pre-arranged list of values)."
Dictionary attacks usually succeed because many users select single words from dictionaries, short passwords (7 characters or less), or simple, predictable word changes (e.g., adding a digit). However, these are easily defeated. Adding a random character in the center can make dictionary assaults impossible.
Cain and Abel Software tool Let's now review the setup dialog's tabs, focusing on most of them:
Sniffer tab
Selecting the Ethernet interface card for sniffing is possible with the Sniffer tab.
ARP tab:
This tab lets us set up ARP poisoning routing to carry out an ARP poisoning attack, which fools the victim's computer by pretending to be another device to obtain all traffic associated with that device—typically the router or a crucial server.
The filters and ports tab
The filters and ports tab show the most common services and the ports they are using by default. You can alter the port by right-clicking on the service whose port you wish to modify and then enabling or disabling it.
Cain's sniffer filters and the TCP/UDP port of the application protocol.
Traceroute tab:
This method counts the number of hops a packet takes from its source machine to its destination machine to calculate the path between two places. Additionally, Cain provides functionality that enables the collection of Whois data, hostname resolution, and netmask resolution.
Tab for certificate spoofing:
A public key certificate, or digital certificate or identity certificate, is an electronic document used in cryptography that binds a public key with identity information like a person's or organization's name, address, and so on — using a digital signature. The certificate can confirm that a public key belongs to a specific person.
A certificate authority (CA) will sign a standard public key infrastructure (PKI) scheme. The signature in a web of trust scheme can be that of other users ("endorsements") or the user (self-signed certificate). In any scenario, a certificate's signatures serve as the signer's confirmation that the public key and identity information match.
Simply put, it can be thought of as some data (public key, cipher suites, and other information about the certificate owner) that contains information about the destination server and is encrypted by trusted organizations (CA) that are permitted to create such data. To ensure that the client application communicates with the correct server, the server transmits its own certificate.
Conclusion
Cain and Abel software are strong tools that crack passwords quite effectively. It can crack almost any type of password, and you will often acquire it in due time. Sniffing the networks allows for recovering different types of passwords using dictionaries, brute-force, and cryptanalysis attacks.
