Tenable Nessus: Best Vulnerability Scanning Tool for Security Professionals
Tenable Nessus ranks as the top vulnerability scanning instrument for professional security work because skilled analysts chose this platform. Discover Tenable Nessus' elementary components and advantages which aid system protection against potential threats effectively.
1/29/20254 min read

Tenable Nessus Vulnerability Scanner
Tenable Nessus vulnerability scanner is a tool for the assessment of any IT infrastructure and network system. It is used to detect and scan security vulnerabilities. It is mostly used by cybersecurity checkers and large-scale organizations for their security purposes.
Who can use it?
Used by software developers*
Mostly used in the testing phase of any software. Software developers ensure the security of software through the Nessus tool to check security weaknesses and drawbacks of front-end and back-end, also in their code and configuration.
It is important before the deployment of the software to the end user. It makes sure the software is secure for individual or organizational purposes.
Work as administrator of security and system
With the help of the Nessus tool, it is easy to locate and indicate weak or outdated software. That can be a big default and threat for any organization.
It is used as an instructive tool to take safety steps to identify vulnerabilities to make strong security checks.
Why is Nessus necessary?
Many drawbacks, weaknesses, and security purposes. The vulnerability findings can be found with this tool within any software.
Easy automation and uses.
This tool has many features due to its friendly user interface. It provides different automated scanning facilities, which help organizations and people from many technical levels
It is much attractive to scanning and mitigating serious vulnerabilities smoothly and effectively.
Identification of Vulnerabilities
With the latest updates, all crackers and hackers fail to gain the benefits of weak vulnerabilities and steal sensitive information of any person or organization.
It is a plus point of this tool that keeps the system updated and identifies the latest vulnerabilities and provides protection and security steps to avoid any data loss and hacking.
Mostly used in the testing phase of any software. Software developers ensure the security of software through the Nessus tool to check security weaknesses and drawbacks of front-end and back-end, also in their code and configuration. For security of any system it is much more important.
Plugin Frame and Flexibility
It is very amazing due to its flexibility and friendly environment of plugins, allowing its users to use custom plugins.
Any plugin of Nessus provides extensibility facilities, so it is very important to provide an environment to use any plugin for the assessment of the system to measure security steps.
Widely Used in Industries
In vulnerability scanning tools, this tool is considered a prominent player among scanning tools.
It is widely used in industries and organizations and by individuals for strong detection and scanning of security drawbacks and weaknesses of any system.
Its continuously satisfactory performance, valid results, and enormous number of features make it widely accepted.
Sure, its authentication and garnered confidence of industries, individuals, and organizations worldwide. It is considered the best choice about scanning vulnerability among professionals and enterprises alike.
Affordable Price
According to comparison with other scanning products, Tenable Nessus’ cost is much more reasonable and provides extra performance, which is a good thing about Nessus to provide services at market rates.
Many Features of Nessus
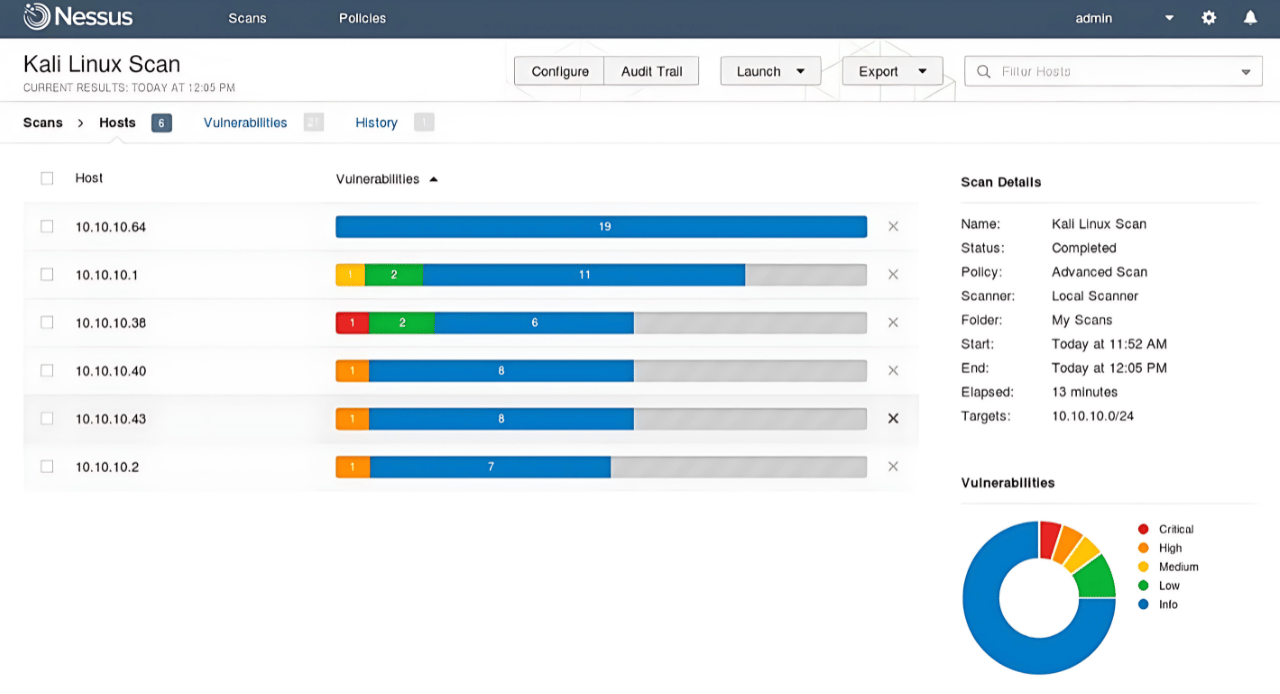
Nessus provides two versions:
1. Nessus Expert


Its prominent features are penetration testing and breaches.
2. Nessus Professional


It is widely used in multinational organizations and security departments.
3. Nessus Docker


In a container, Docker Image enables deployment. With the help of two versions, one is Tenable Nessus Scanner and Tenable Nessus Professionals. Oracle Linux 8 and Ubuntu are two images provided by Tenable Nessus and used for selected settings of the image.
Working at Nessus in Cybersecurity
For scanning and vulnerability assessment, Nessus is widely used in the world for cybersecurity.
Threats, vulnerabilities, and hacking in cybersecurity are controlled by Nessus.
Some important and widely used features of Nessus in cybersecurity are as follows:
Key Feature
Management of vulnerability
Overcome risks!
Thorough scanning
Continuous assessment
Security control
Updating system
Detailed information about vulnerabilities
Ecosystem
Precautions
How to Download and Use Nessus?
Tenable Nessus is a widely used subscription-based tool.
To use Tenable Nessus, first buy a subscription according to your need and usage. After installation of Nessus, the vulnerability scanner comes in the form of nessuscli.exe, an executable file.
Steps:
1: Buy Installation Subscription
First, buy its subscription for installation from its official and authentic website. According to your device's operating system, try to download the latest version to experience its best features.
It can be downloaded in three ways:
Virtual Machine
Docker
Custom
Tenable Nessus Professional subscription
2.Installation Instructions
After buying the subscription, fulfill all instructions to download and install it on your device according to the provided operating system.
Now start Nessus with an easy task. It will direct you to a localhost webpage.
3. Nessus Activation
After starting, a prompt will appear around product activation.
Create a Tenable account as required. Provide the product for activation and get an activation code to activate your product.
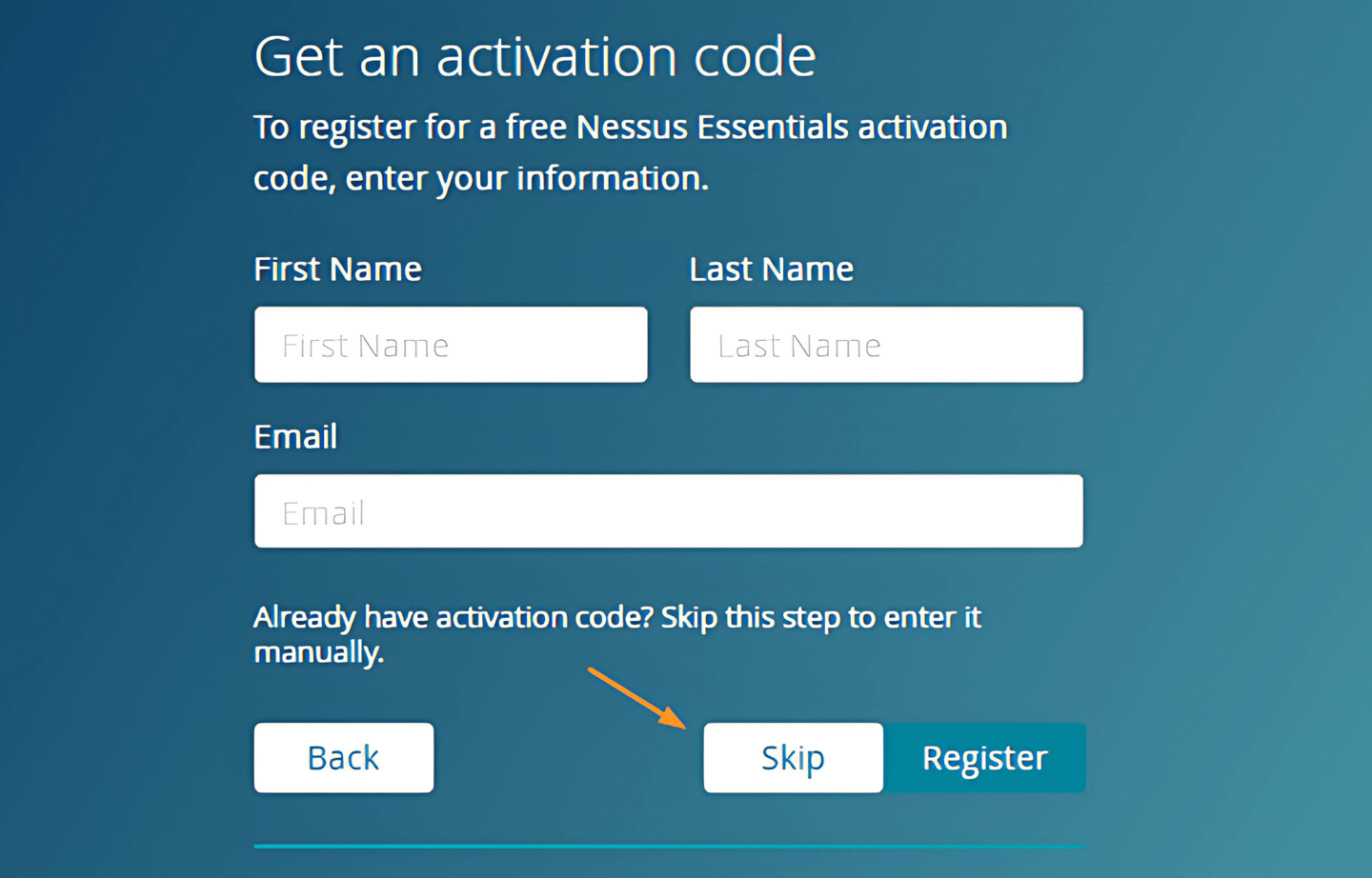
4. Nessus Configuration
After activation, with the help of the wizard, create a user account. After account creation, start downloading and setting up plugins.
You will then be redirected to the Nessus professional dashboard.
If not, wait for some time because the installation of plugins is time-consuming.
After completion, you can check the menu bar for a loop icon before the "Resource Center" option appears.
Conclusion
In vulnerability scanning tools, Tenable Nessus vulnerability scanner tool is considered a prominent player among scanning tools. It is widely used in industries and organizations and by individuals for strong detection and scanning of security drawbacks and weaknesses of any system. It is widely used in industries and organizations and by individuals for strong detection and scanning of security drawbacks and weaknesses of any system. Its continuously satisfactory performance, valid results, and enormous number of features make it widely accepted. According to comparison with other scanning products, Tenable Nessus’ cost is much more reasonable and provides extra performance, which is a good thing about Nessus to provide services at market rates. It is much attractive to scanning and mitigating serious vulnerabilities smoothly and effectively.
